In this blog post, we will walk you through 6 easy ways to combat phishing attacks and improve security online. In our interconnected world where technology plays an integral role in our daily lives, cyber security awareness and phishing prevention is more crucial than ever. The digital landscape is full of threats, and one of the most pervasive and effective techniques hackers use to access your data is through a phishing attack.
Hackers will attack for various reasons. Some cybercriminals may engage in hacking for personal gain, while others will attack for a cause that aligns with their beliefs – “Hacktivists” who may take part in Advanced Persistent Threats (APTs) that seek to gain access to a system and embed themselves, often undetected for an extended period of time. Others just do it for fun. Regardless of the reason, cybercrime has become a lucrative business for cybercriminals. According to Wired Magazine, an estimated $1.1 billion was lost to ransomeware payments in 2023 alone.
What is a Phishing Attack and How to Protect Your Business
Hackers will often target your business through ransomware (a single type of malware); a (D)DoS attack where the hacker will flood a network with fake activity in order to overwhelm it; phishing and other social engineering attempts, malware, password attacks, website and webapp attacks. All of these methods can cripple your ability to operate and potentially destroy your IT equipment. In order to minimize risk, it’s helpful to know how they will attempt to gain access.
If you’re a business, hackers will often look for entry through your employees because it is the easiest way to gain the most control over your system. Hackers often utilize phishing campaigns or other forms of social engineering to fool employees into providing their credentials, downloading malware, giving away remote access to their computers, clicking on fake links or transferring money. These attacks have a high success rate and can cause significant damage, especially if the hacker is able to exploit an employee with higher permissions. For many hackers, phishing and social engineering attacks produce the highest ROI.
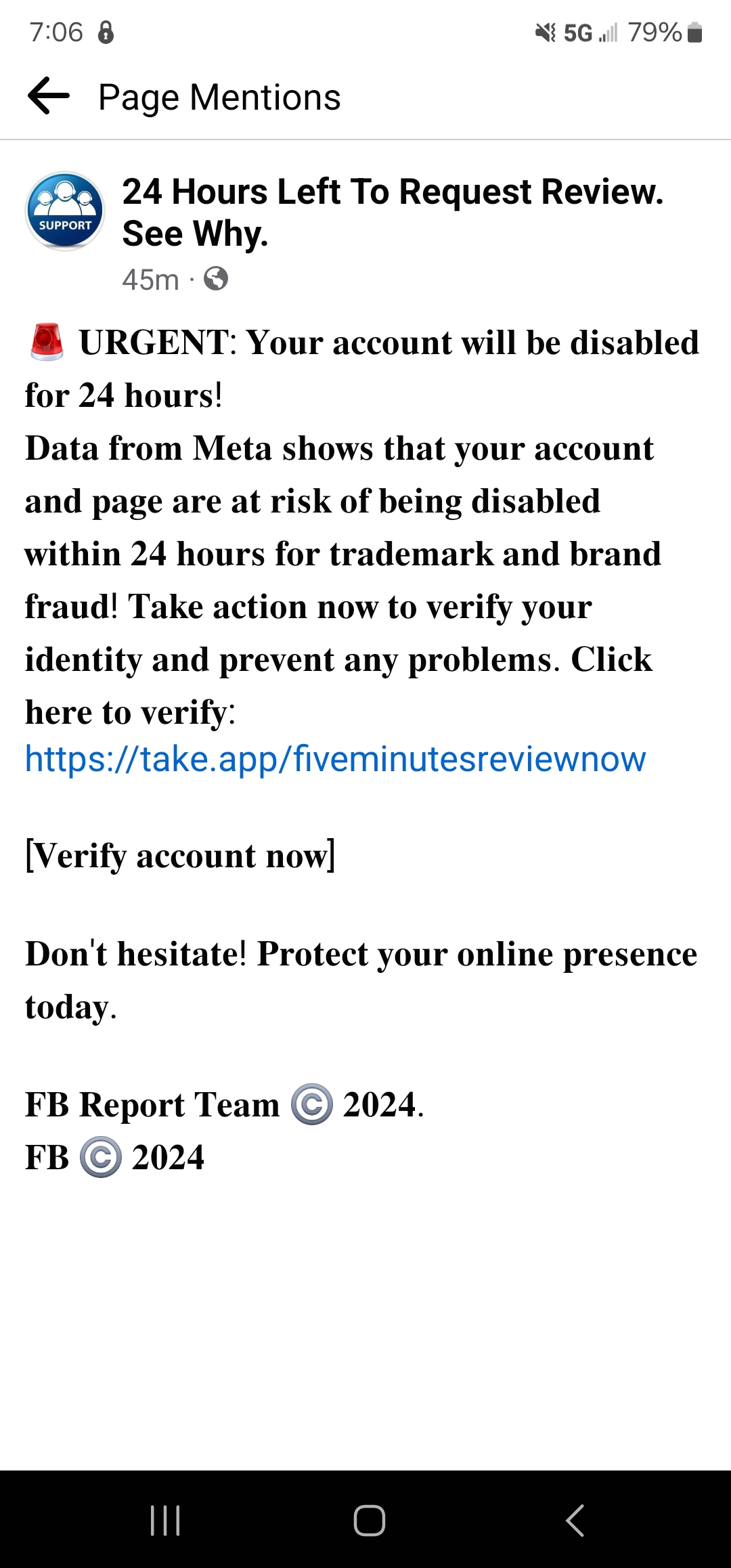
For example, cyber criminals will often attempt to gain access through business social media accounts. A popular phishing scam that has been gaining traction in 2024 is a Facebook copyright infringement scam.
Facebook users (both personal and business accounts) have reported receiving messages notifying them that content they have posted to their page violates trademark or copyright laws, and that their account will be permanently disabled if they do not take action within 24 hours or less. The fake notice typically directs the account owner to click on the provided link to file a “quick” appeal or correct the issue in some other way. The link does not lead to a legitimate Facebook-related page. Instead, it leads to a site that is designed to harvest the unsuspecting account owner’s login credentials. Once the hackers had the user’s credentials, some were even able to access credit card information. Organizations that rely on their Facebook page for advertising and communicating with customers could be targeted specifically as it provides another access point into a company’s data.
While the scam in this example is fairly easy to spot, some variations are more sophisticated. If you receive a suspected phishing message, pause and read the message again carefully. Do you notice any typos, aggressive or unprofessional language, and brand inconsistencies such as grainy or inconsistent logos? If so, it’s likely a scam.
Another way to tell if the communication is legitimate requires a careful look at the sender and delivery method. A legitimate Facebook representative will never send you a message from a personal account. Additionally, Facebook will never send you a direct message or comment on your post.
If you are being strongly pushed to click on a link, resist the urge to do so. Never click on the link provided in the message. In this example the link points to a fake Facebook page.
If there is a legitimate concern with content on your page, an official Facebook communication will appear in the Notifications section of your account. If at any time you feel you may have been hacked, contact facebook.com/hacked to report the incident.
These types of phishing attempts try to trick you into acting quickly, creating a false sense of urgency that pushes you to respond before you’ve had a chance to mentally process and verify the legitimacy of the request for information. They often pose as a true customer, service provider, law enforcement or government agency, and their goal is to trick you into providing important information that will enable them to gain access to your system.
Training your employees how to better spot phishing emails and to be conscious of their own internet footprint is key to mitigating these types of attacks. Remember to look for:
-
- Anything that feels phony or gives you pause
- Errors in punctuations, formatting, typos, grammar or generally awkward language
- Inconsistencies in tone or verb tenses are warning signs.
- Inconsistencies between the sender’s name, signature and email. If it seems like something you would not expect to see from a particular sender, it’s likely a hacking attempt.
- Fake links that are designed to mimic a legitmate address or confuse (example: “lin.kedin” instead of LinkedIn). Legitimate companies are very specific about their brand guidelines and would not send out a communication that deviates from a carefully curated style.
- The use of scare tactics to pressure you into acting quickly or immediately.
Cybersecurity Best Practices: 6 Easy Ways to Combat Phishing
Phishing attacks have become increasingly sophisticated and prevalent. Cybercriminals constantly devise new and creative methods to trick individuals into revealing sensitive information or clicking on malicious links. To safeguard your digital information, it’s important to stay informed about the latest cyber threats and adopt proactive measures. Let’s dive into these 6 easy ways to combat phishing attacks and improve your online security.
1. Educate Yourself: Cyber security awareness starts with education. Learn to recognize phishing attempts, which often arrive in the form of deceptive emails or messages with a high sense of urgency. Be wary of unsolicited emails and social media messages requesting personal information, money, or login credentials within a short timeframe.
2. Verify the Sender: Always double-check the sender’s email address. Cybercriminals often use email addresses that mimic legitimate organizations. Ensure the sender’s domain is accurate, and the email isn’t misspelled. If the request is coming through a social media channel, pay close attention to the sender’s account handle.
3. Think Before You Click: Never click on links or download attachments from suspicious sources. Hover over links to preview the URL, and ensure it is directed to the correct website. Hover, but don’t click.
4. Use Strong Passwords: Employ strong, unique passwords for your online accounts. A password manager can help you generate and store complex passwords securely.
5. Enable Two-Factor Authentication (2FA): Implement 2FA whenever possible. We understand it creates an extra step, but that extra step provides an extra layer of protection, making it more challenging for attackers to access your accounts.
6. Keep Software Updated: Regularly update your operating system, antivirus software, and applications. These updates often contain crucial security patches. An outdated operating system is like leaving a window cracked open for a cybercrimal to enter through and gain access to your data.
If you suspect a phishing attempt, one of the best things you can do is seek verification from a trusted source. For example, if you receive an email from your supervisor asking for your login credentials to a work portal immediately to address an urgent work situation, it’s ok to pause and get confirmation. Instead of replying to the email, make a quick call to your Supervisor and IT team to confirm their request.
How We Can Help
By adopting these best practices, you can significantly reduce your vulnerability to phishing schemes and enhance your overall online security. It’s an ongoing process that requires vigilance and education, but staying informed and cautious can help protect your digital presence. And yes, if you have questions, we can help.
Now that you’ve armed yourself with this valuable information on cyber security awareness and phishing prevention, it’s time to take the next step in fortifying your online defenses. Our team is here to help you assess your current security position and recommend personalized strategies to safeguard your digital assets. If you are interested in learning more about our IT consulting services and how they can benefit your organization, contact us today.

Apple iOS 15 & iPadOS 15 Overview
June 2022 - Apple announced the release of the public beta for iOS 15 and iPadOS 15, set to release fully to the public fall of 2022. There are not many large-scale changes in iOS 15, rather the updates appear to be directed towards making existing capabilities more...
Latest Smart Homes News
Biamp 2024 Lineup Delivers Best in Versatile AV Solutions
What do corporate conference rooms of every size, stadiums, performing arts venues, outdoor community spaces, courtrooms, and government offices all have in common? A need for the best in versatile AV Solutions, with high-performing, customizable and scalable systems...
Latest Project

Alive Video Wall Displays Deliver Immersive Experience
Alive Video Wall Displays Deliver Immersive Experience through massive video wall and purposeful use of color in every fitness room.